How to Choose the Right ACS for Your ISP
After working with TR-069 across dozens of environments, I’ve seen the difference a good ACS can make. It’s not just about having a dashboard that talks to routers—it’s about how well your infrastructure, support team, and growth plans align with the tool that’s supposed to manage your fleet.
Choosing an ACS isn’t just a technical decision. It’s a business-critical one. If you pick the wrong one, you’re going to hit scaling walls, fight with unreliable data, and burn hours chasing device behavior instead of solving customer problems. If you choose the right one, your team becomes faster, your customers stay happier, and your operations scale without headaches.
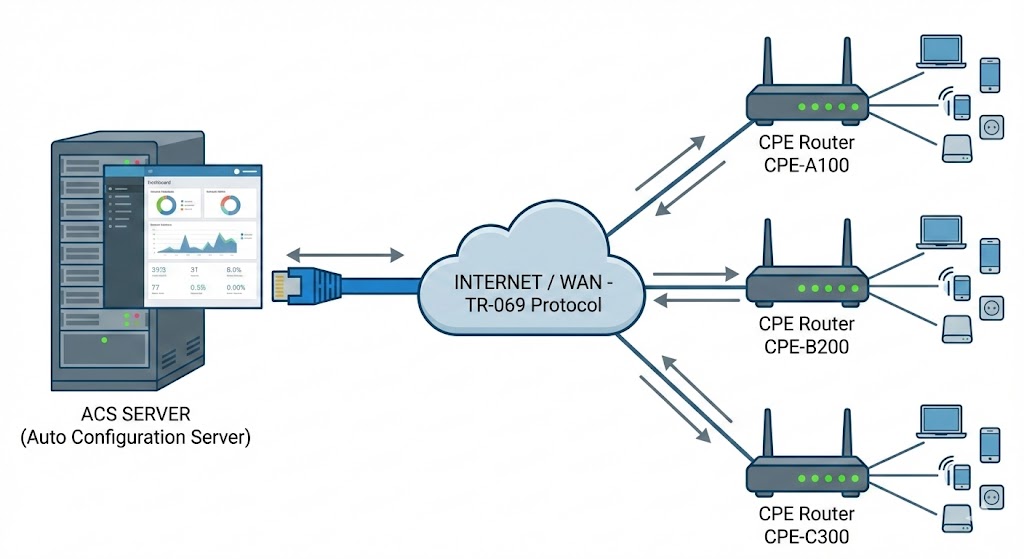
The first thing to understand is that not all ACS solutions are the same. Some are open source, some are commercial. Some are built for flexibility, others for simplicity. Some are stuck in the 2010s and others are evolving to handle TR-369 (USP) and telemetry at scale.
Before even testing options, you need to know what you actually need from your ACS. Are you just trying to provision a device with the correct PPPoE username and password? Or do you want to build a system that can pull signal strength, latency, device usage, and send real-time diagnostics to your support team? Are you managing a few thousand routers, or planning to hit hundreds of thousands across different vendors and models?
Scalability
Scalability is one of the most important—but most overlooked—factors. Many ACS platforms start fast and feel fine when you’re managing 500 devices. But when you hit 20,000, 50,000, or more, their performance breaks down. Polling becomes unreliable. Connection requests hang. Some devices stop reporting. Then your support queue fills up, and the whole point of automation is lost.
True scalability isn't just about handling a large number of devices—it's about maintaining performance under real-world conditions where demand is unpredictable and uneven. ISPs don't operate in steady-state environments. You face dramatic usage peaks during mass firmware rollouts, when storms knock out power and thousands of devices reconnect simultaneously, or during customer onboarding campaigns where hundreds of new CPEs come online in a single day. Your ACS needs to handle these surges without choking, which means intelligent queuing, prioritization mechanisms, and the ability to throttle non-critical operations during high-load periods.

The architecture of your ACS deployment matters enormously at scale. A monolithic, single-server setup might work for small operations, but growth demands distributed architectures. Can your ACS scale horizontally by adding more worker nodes? Does it support load balancing across multiple instances? Can you deploy regional ACS clusters to reduce latency and improve reliability for geographically dispersed networks? Some ISPs operate across multiple states or countries—having the ability to distribute your ACS infrastructure closer to your devices improves response times and reduces the impact of network partitions or data center outages.
Regional deployment also intersects with compliance and data sovereignty requirements. Different countries and regions have varying regulations about where customer data can be stored and processed. GDPR in Europe, LGPD in Brazil, and other data protection laws may require that device configurations, diagnostic data, and customer information remain within specific geographic boundaries. A scalable, modern ACS should support multi-tenant or multi-region deployments that allow you to segment data according to regulatory requirements while maintaining centralized visibility and control where permitted. This becomes critical if you're operating across borders or planning international expansion.
Performance under peak load also depends on how efficiently the ACS handles periodic tasks. TR-069 involves constant communication—inform messages from devices, periodic polling for metrics, configuration updates, and diagnostic requests. At scale, poorly optimized polling strategies can create thundering herd problems where all devices try to check in simultaneously, overwhelming your infrastructure. A well-designed ACS staggers these operations, uses intelligent scheduling, and implements backoff strategies when devices are unreachable, preventing cascade failures that bring down your entire management plane.
Vendor Agnostic
Another issue is how the ACS handles vendor-specific behavior. TR-069 is a standard, but vendors implement it differently. Some hide parameters, some respond incorrectly, some don’t follow the specs at all. A solid ACS doesn’t just fail silently—it logs, retries, and adapts. It should have a way to normalize different device types so you can treat your network consistently, even if your fleet is a Frankenstein of different brands and firmware versions.
Being truly vendor-agnostic means more than just claiming TR-069 support—it means your ACS can work seamlessly with any CPE manufacturer, regardless of how they've interpreted the standard. In the real world, ISPs rarely have the luxury of a homogeneous fleet. You might be deploying TP-Link ONTs in one region, Huawei routers in another, and inheriting a legacy install base of Zyxel, Intelbras, or Technicolor devices. Each manufacturer has their own quirks: different parameter naming conventions, varying support for optional features, inconsistent firmware behavior across models, and sometimes outright bugs in their TR-069 implementation.
A vendor-agnostic ACS acts as a universal translator for your network. It maintains profiles and mappings for different device types, so when you want to configure WiFi settings, you're not writing different workflows for each brand—you're using a unified interface that knows how to communicate with each one properly. It handles the differences in data models, compensates for missing features by finding workarounds, and gracefully degrades functionality when certain capabilities aren't available on specific hardware.
This flexibility is critical for future-proofing your operations. When a new vendor enters your supply chain—whether by choice or necessity due to chip shortages or better pricing—you don't want to rebuild your management infrastructure. Your ACS should onboard new device types with minimal configuration, allowing you to test, deploy, and manage them alongside your existing fleet without disrupting operations or retraining your team. True vendor agnosticism gives you negotiating power with suppliers and operational resilience when the market shifts.
User Interface
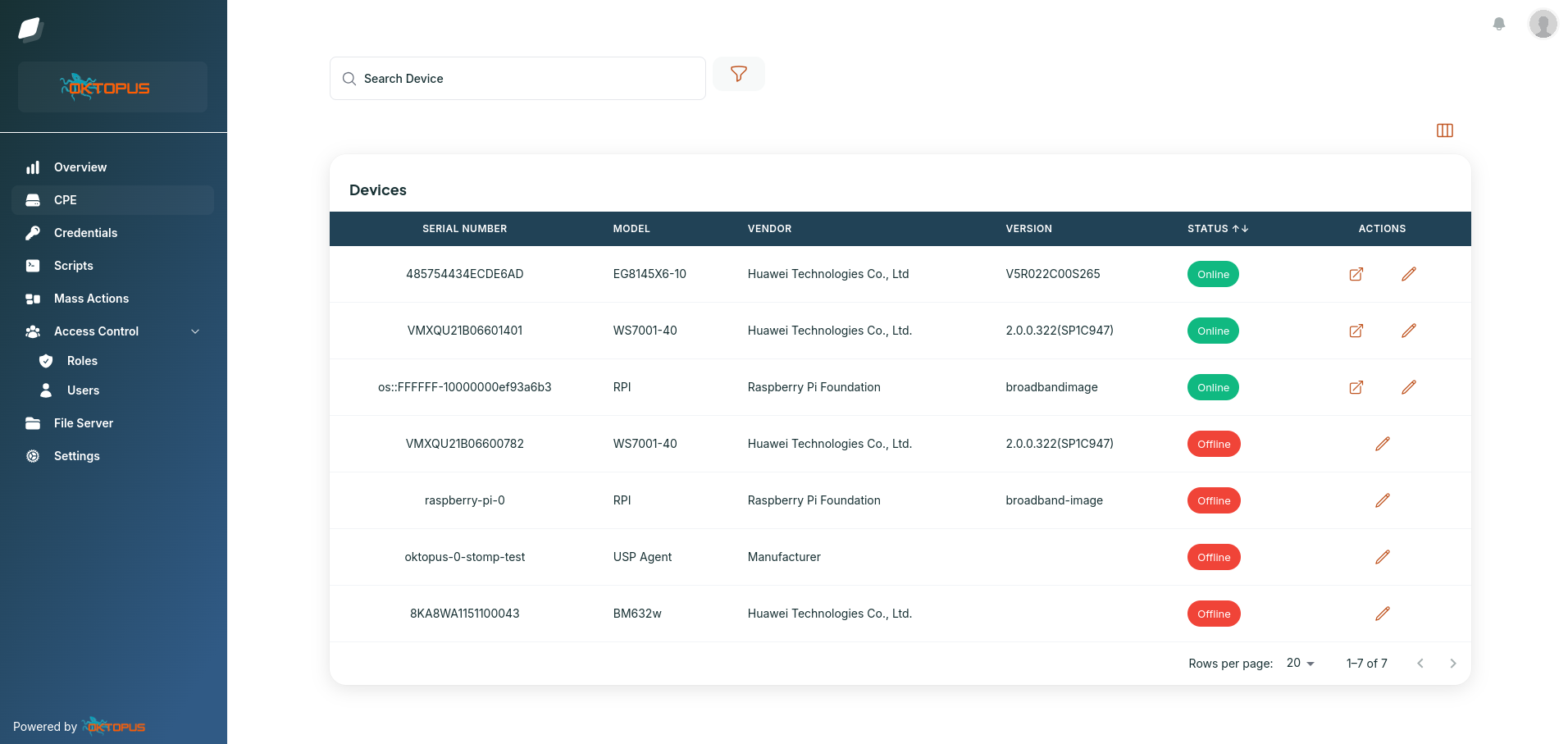
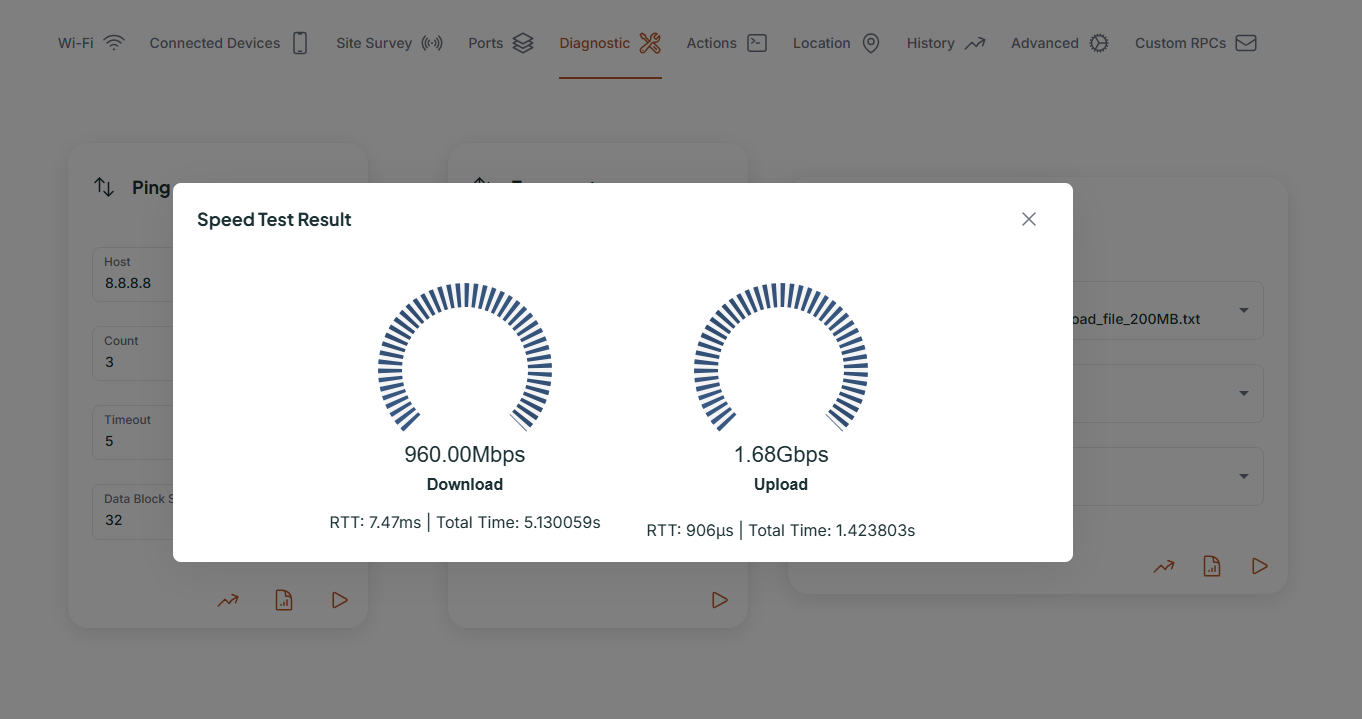
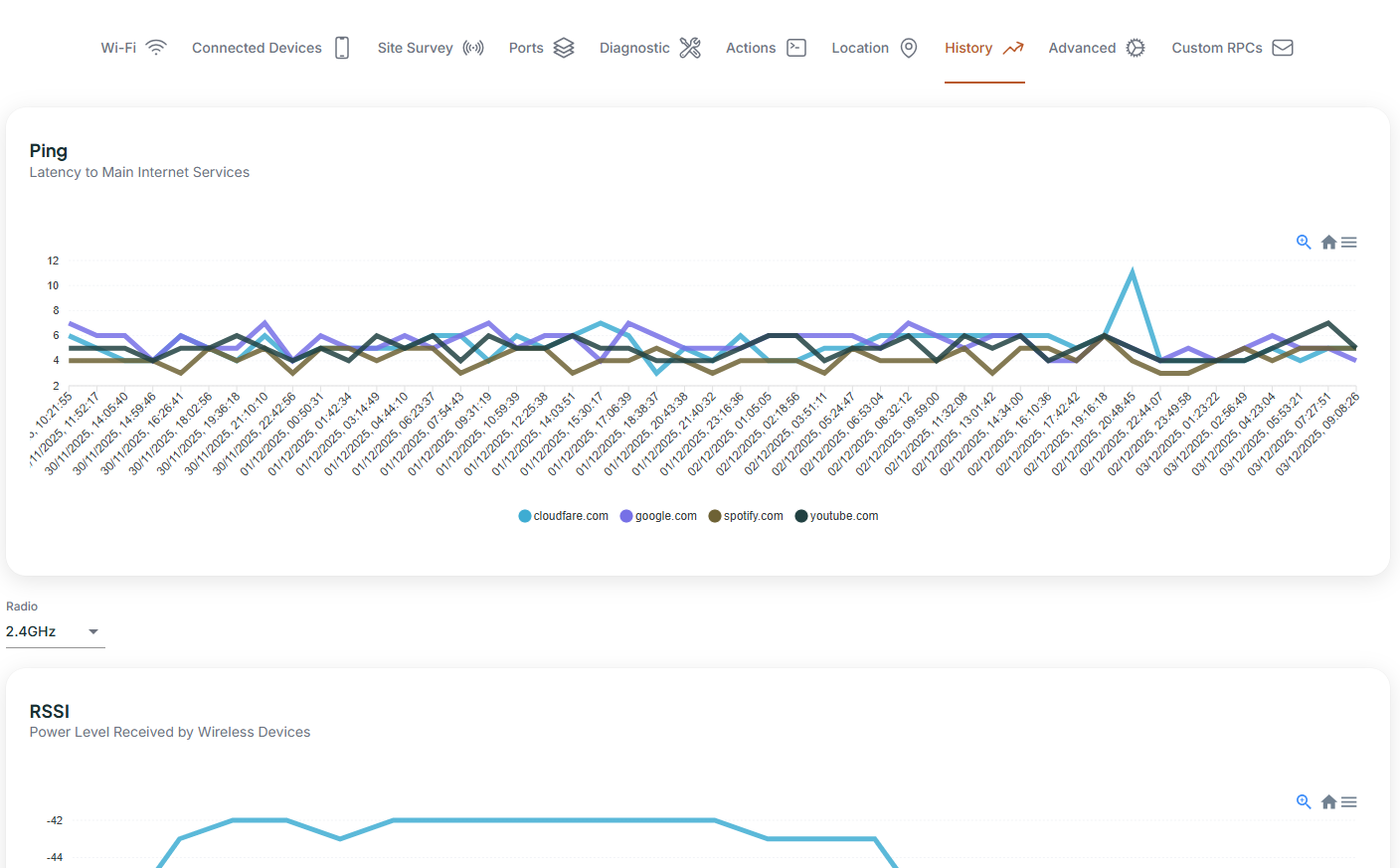
Then there’s the interface. I’ve seen ACS platforms that require operators to craft raw SOAP payloads just to reboot a device. That’s not sustainable. Your ACS should offer an API, yes, but it also needs a clean, intuitive UI where your support agents can take action in seconds. Ideally, it should also show real-time or historical device metrics, offer filtering, and allow bulk actions without needing a sysadmin on standby.
.jpg)
Security and Ecosystem
Security should be non-negotiable. The ACS is the control tower of your subscriber network. If it’s compromised, the attacker controls your routers. Make sure your ACS supports secure connection request mechanisms, encrypted data storage, proper access control, and audit logs. Bonus points if it can handle certificate-based authentication and push configurations that improve the security posture of the CPEs themselves.
Support and ecosystem matter, too. Are you going to be left alone fixing bugs in some legacy open-source project? Or is there an active team that understands ISPs and can respond quickly when a firmware update breaks TR-069 on a certain vendor’s line?
Integration
Finally, think about extensibility. Can you integrate the ACS into your CRM, ticketing system, or monitoring pipeline? Can you use it to trigger actions based on real-world problems—like automatically rebooting devices with high CPU, or alerting your team when signal strength drops below a threshold? An ACS should be a platform, not just a panel.
Conclusion
At Oktopus, we’ve seen ISPs come in from chaotic setups—some juggling multiple ACSs, others relying on half-working scripts—and transform their operations by centralizing control, visibility, and automation. It’s not just about saving time. It’s about gaining real control over your network and delivering a better experience to your customers.
If you’re evaluating ACS solutions, my advice is to stop looking for a checklist of supported parameters and start asking whether the ACS helps your team move faster, with confidence, across your entire device fleet. That’s the difference between a tool and an asset.
Take control of your
network today
The world’s most widely used USP Controller and TR-069 ACS, with
enterprise-class features and no vendor lock-in.