What is the TR-069

Understanding the TR-069
Battle-Tested Remote Management for ISPs
If you work with ISPs or need to manage CPEs at scale, you’ve probably come across the acronym TR-069. It stands for “Technical Report 069,” but is also known as CWMP (CPE WAN Management Protocol). It’s one of the technologies that quietly powers a lot of what keeps the Internet's last-mile delivery running efficiently behind the scenes.
At its core, TR-069 was designed to solve a problem that every ISP faces as it starts to grow: how do you manage thousands, or even millions, of devices deployed in customer homes/businesses without relying on manual configuration, on-site technicians, or customer input? The idea is simple, although how it works technically may not be so (we will go back to this in another post).
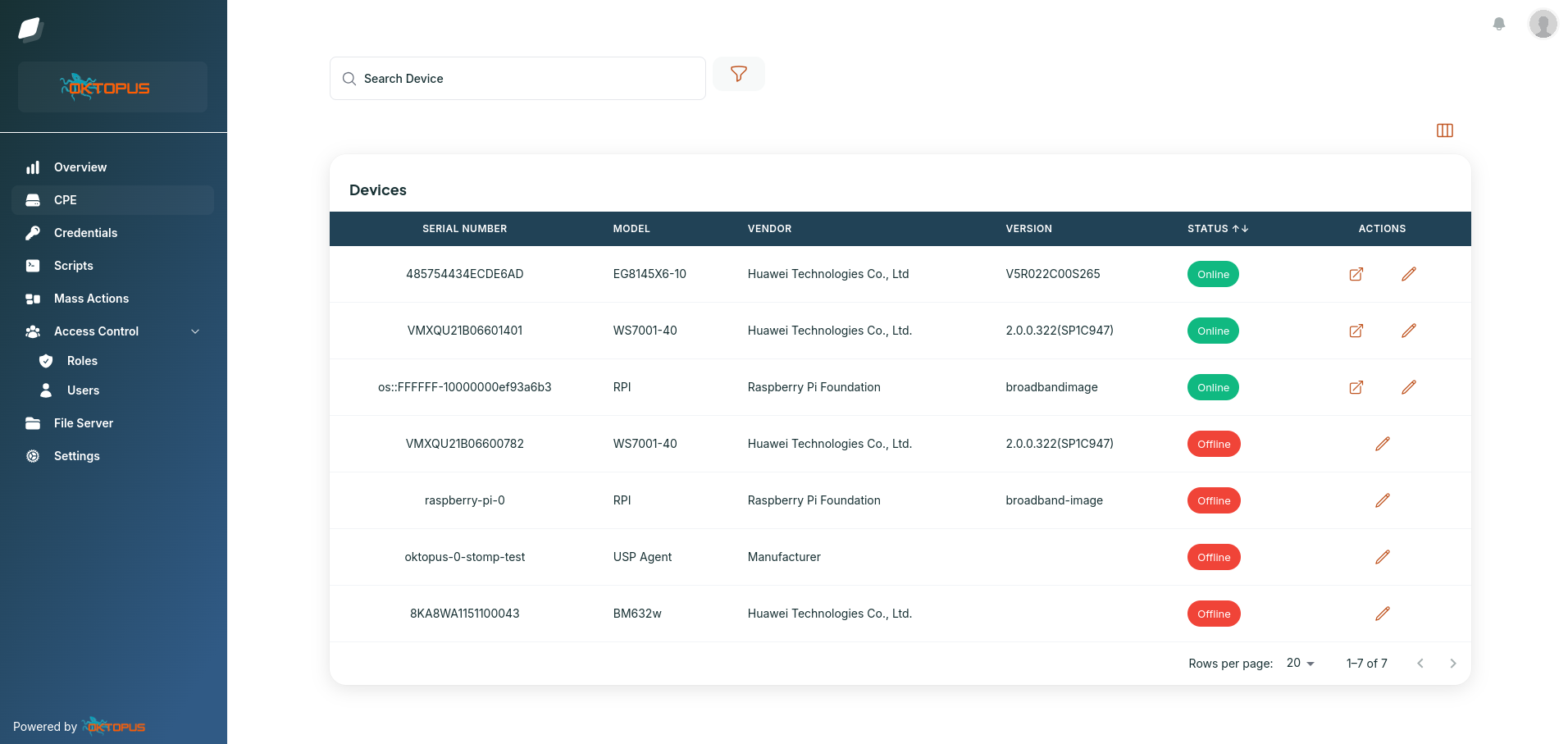
When a customer or technician plugs in a router, modem, or any other customer premises equipment (CPE), that device can reach out to a central server—called an ACS, or Auto Configuration Server. From there, the ACS can provision the device, update its firmware, configure its wireless settings, monitor its performance, and even reboot or reset it if needed. All of this happens without the end-user needing to touch anything.
Advantages
This remote management capability makes TR-069 incredibly valuable for ISPs. It reduces support calls, prevents unnecessary truck rolls, and allows technical teams to act precisely. Instead of asking a customer to check the router state or trying to guess the problem based on vague symptoms, a technician can query advanced data, gather logs, and even push a fix, all from a remote interface.
Another big advantage of using this amazing standard is that it works with different manufacturers, because it was created by Broadband Forum, also known as BBF, which is a non-profit organization made up of multiple operators and industry-leader companies that have joined forces to create standards that push the industry progress.
Adoption
Even though the CWMP has been around for a long time (~20 years), it’s still widely used today. There are tons of reasons for it: most routers shipped in the last decade support TR-069 out of the box, and it’s not financially viable to change this whole hardware infrastructure; it works pretty well for most cases, and just like every technology, it has a curve of adoption and deprecation.
Most old and new CPEs have support for the standard, differing only in amendments, versions of release, and data models (TR-098 and TR-181), which have been released throughout the time to keep pace with new challenges and the Internet scenario evolution.
While newer protocols like USP (TR-369) are making their way into the market, TR-069 remains the default for a huge portion of deployed infrastructure. What we might see in the next years is probably going to be very similar to what is happening now with IPv4 vs IPv6 dual-stack operations and evangelization work, although with a more radical competition bias.
As ISPs start to modernize their stack with TR-369 and other worth mentioning technologies like RDK-B, prplOS, and OpenWRT that are becoming each time more common and accessible, it will drive an increase adoption of these, based on market competition, that will put ahead the businesses who are capable to deploy this stack, to increase efficiency, reduce costs and deliver much better services than its competitors.
Public Target
Each ISP has its own challenges, based on where they’re located, broadband network architecture (FTTH, DOCSIS, FWA), the size of their subscriber base, and other factors. TR-069 for remote CPE management has benefits to all of them, because of its agnostic nature of the underlying medium access and ROI (Return on Investment).
Tier 1
Managing millions of devices across large and complex networks with legacy infrastructure mixed up requires a lot of creativity to maintain consistent customer service. While CWMP is a great ally, it is needed to oversee a platform implementation that can abstract underlying technologies to keep up with the same UX and not sacrifice new technology advances.
Any small enhancement in the process or in the ACS causes a big impact due to the scale of the operation. So it's worth taking into account a broad TR-069 implementation with support for multiple amendments, data models, and so on; it makes sure that no device is left behind, and all the fleet works seamlessly across its heterogeneous environments.
It’s nice to have advanced features built on top of the device management core platform to gather analytics, integrate data with existing OSS/BSS, and maintain complex workflows and automations.
Tier 2
While on this stage, there’s a lot of room to optimize costs, architect new infrastructure, and plan how to maintain the old. There’s already a considerable scale and growth, but still, the opportunity to act quickly or at least to be more agile than big companies, so it’s easier to make decisions first and stay ahead.
It’s an important stage to define the company's approach, from a business and technical point of view, and each of these will play a part in the other to support the long-term sustainability.
Tier 3
The best stage to start implementing the TR-x69 protocols. The solutions are very cheap, can be used in the cloud or on-premises, and some ISPs even opt to use open-source or in-house options.
It’s crucial to have an ACS solution to grow the customer base while not having a linear increase in support staff and to maximize manpower while resources are probably scarce and will require proper scaling in the future.
For all ISPs, TR-x69 standards allow to play big while staying “lean”.
Security
The protocol itself works over HTTPS, with the router reaching out to the ACS on a scheduled basis, or in response to events like a reboot or network change. Communication is handled via SOAP/XML messages, and while the protocol was designed with security in mind, real-world deployments vary a lot. Some devices are properly secured with certificates or strong credentials, while others ship with default usernames and passwords—or worse, no authentication at all. That’s why it’s so important to validate the security posture of any CPE you plan to manage remotely.
In practice, working with TR-069 can be tricky. Different vendors implement it slightly differently, which means a one-size-fits-all ACS might not behave consistently across your entire fleet. Some routers will respond perfectly to parameter queries, while others might time out, return malformed data, or simply ignore certain commands. That’s where having a solid ACS solution becomes critical—not just one that handles basic provisioning, but one that can adapt to device variations, offer diagnostics, and scale with your subscriber base.
Implementations in Practice
There’s only one standard document source of truth, but many dialects of different vendors that interpret or build different TR-x69 implementations. It means that devices, although they support the same protocol, in the real world, there are many caveats to take care of. Including (which is the most common case), different data models with extensions and vendor-specific parameters.
As a result, building a one-size-fits-all ACS becomes a major challenge, especially in multi-vendor environments, which is the norm for most ISPs.
Open Source
Building an ACS solution is time-consuming, and “time is money”. Luckily, there are open-source solutions that can help with that. Especially in the initial stages, if you want to test and learn about the protocols or even use them in production, it’s a nice start.
Many ISPs, mainly at the beginning of their operation, opt to go with an open source solution that comes with no cost.
But, before making your choice, think about whether you have internal technical know-how, infrastructure servers and people to keep up with the overhead work of installation and maintenance associated with it, the time-to-market, your core business, pros and cons of each option, like features, support, SLA, and put it on paper to find out the TCO (Total Cost of Ownership) of the platform and if it’s sustainable along the time.
Paid Solutions
Some of the open source options also offer paid versions of their software and commercial support. Another companies offer full proprietary solutions. Hiring a paid platform should provide the ISP with a comprehensive solution that “just works” and has advanced functionality to boost its operations, fully integrated into the company workflow.
Each vendor in each region of the globe has different approaches to the software stack, architecture, deployment options, and pricing. Over time, offerings have become more accessible and granular, which means ISPs can choose a price that fits their budget and features that really matter to their use case.
—
At Oktopus, we’ve embraced TR-069 not just as a legacy protocol we support, but as a core part of how we help ISPs manage their networks more intelligently. By combining device visibility with powerful automation (including zero-touch provisioning), we give operators the tools to deliver better service without increasing support overhead. TR-069 isn’t just about remote configuration. It’s about transforming support from a reactive cost center into a proactive engine of customer satisfaction.
So if you’re running an ISP and still managing devices manually—or relying on outdated processes that don’t scale—it's probably time to give TR-069 another look. The protocol may not be new, but in the right hands, it's still one of the most powerful tools you can have.
Take control of your
network today
The world’s most widely used USP Controller and TR-069 ACS, with
enterprise-class features and no vendor lock-in.